AN AUSSIE SCARE
October 1, 2022 | Expert Insights

Australia is home to some of the most dangerous creatures on the planet. Yet these creatures do not threaten the population as much as cybercriminals do. On September 22, Australia’s second-largest telecom provider Optus announced that it was hacked. Initially, the company did not disclose the extent of the breach. Later it was declared that personal data of nearly 9.8 million users (more than 40 per cent of the population) was compromised. The stolen data included the addresses, date of birth, mail IDs, driver’s license numbers, and passport numbers of consumers.
The hacker announced a ‘heist’ on a popular hacking website under the alias “optusdata,” demanding a ransom of USD 1 million for the stolen data of 11 million users. Once Optus refused to pay the ransom, the hacker released the data of 10,200 users on the internet. Soon after, in an unlikely turn of events, the hacker announced that he would delete all the stolen data and apologised for the hack. The hacker remains anonymous to date.
The recent hack is not the first time Optus has witnessed a data breach. In 2013, the company accidentally leaked the data of 1,22,000 users. The company has also come under scrutiny in the past for its data privacy measures.
The attack on Optus clearly shows the vulnerability of critical infrastructures to hacks. Despite rapid progress in cybersecurity, threat actors have found novel ways to infiltrate unsuspecting businesses.
Background
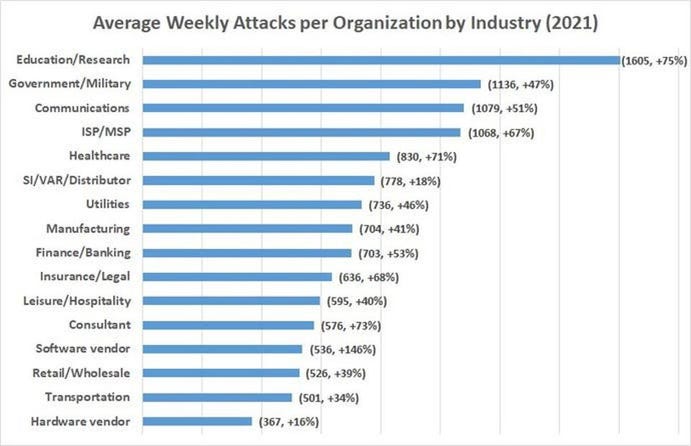
Since the pandemic, cyberattacks on critical infrastructures have skyrocketed. In addition, the anonymity of the internet, large payouts, bad security practices, and ineffectiveness of law enforcement agencies have provided cybercriminals multiple reasons to grow their craft. According to researchers from Cybersecurity Ventures, the global cost of cyberattacks is expected to increase by 15 per cent (roughly USD 10.5 trillion) in 2025. Most often, human error is the cause of the breach, not malfunctioning systems.
In the case of Optus, the attack started with an Application Programming Interface (API) misconfiguration. An API allows two different parts of the software to communicate with each other. When an API was left open without authorization protocols, the hacker used it to infiltrate the system. Since most companies use cloud-based solutions to store their data, the hacker could access a vast trove of customer data. However, the operational capabilities of Optus remained unaffected during the hack.
Analysis
The hack comes when large corporations have been accused of unnecessarily hoarding user data. Governments worldwide are trying to bind private firms with heavy data protection laws, whereas private firms are trying their best to find loopholes in the existing legislature. Unfortunately, Optus had stored customers' data from 2017, including former customers, raising serious concerns over its data privacy policies.
The attack on Optus will force the Australian government to intervene and change its existing data protection laws. Fines imposed on businesses for negligence will be increased substantially. Local law enforcement agencies will work in tandem with the FBI due to the scale of the attack and the involvement of other nationals. New Zealanders, in particular, would be the second-most impacted by the hack due to their extensive use of Optus services. Optus did the right thing by refusing to pay the ransom since it would have only encouraged more attacks in the future.
Despite the hacker announcing that he had deleted all the stolen data, there is a good chance it might be a publicity stunt to reduce the heat from law enforcement agencies. However, if the hacker has already found buyers and sold the stolen data, Australia could witness large-scale phishing campaigns in the coming days. The phishing campaigns would inevitably result in thousands of citizens losing their hard-earned money.
Even with Optus informing law enforcement agencies and the public immediately after the hack, the coordination between private and public players needs to be improved for better response times. Lawmakers must also ensure that financial institutions are informed of ongoing hacks so that they can freeze or flag accounts used in collecting the ransom.
After a preliminary investigation, Optus discovered that the IP address used by the attacker originated from Europe. Unless the Australian government has good ties with governments in other countries (with relaxed extradition laws), it would not be able to find the perpetrator, let alone bring him to justice. On the other hand, a country like the U.S. can exercise its hegemonic status to arrest, extradite and punish criminals outside its territory.
Assessment
- International cooperation is of great importance when it comes to cyberattacks. Unfortunately, the global community is yet to make a unanimous decision regarding the threats posed by cyberattacks. With attacks becoming more prominent and frequent, it will only be a matter of time before other countries suffer the same fate as Australia.
- Telecommunications companies need to invest more in Artificial Intelligence (AI) and Machine Learning (ML) solutions that can automatically detect and deter intrusions within the network.
- While in the recent case, the breach has occurred in a private telecom company, the government cannot absolve itself from its responsibilities. Data theft is as much a cognisable offence as homicide and armed robbery and must attract a matching response from the state law enforcement agencies. While private companies must allocate more resources toward cybersecurity measures, including training staff on good security practices, the government must make citizen-centric cybersecurity a state priority.








Comments